SCAM AWARENESS EDUCATION SERIES
Scammers Impersonate Legitimate Companies
Let’s take a look at how scammers regularly impersonate legitimate companies. Imagine logging into your bank or favorite online store, only to find out later that the “official” site you visited was a perfect digital forgery designed to steal your life savings. This is the reality of website cloning, a highly effective social engineering tactic that has become a cornerstone of modern cybercrime.
What is a Cloned Website?
A cloned website is a near-perfect replica of a legitimate site, created using automated tools that “scrape” the original’s HTML, CSS, and images. While traditional phishing might use a messy, amateur-looking page, cloning is a “copy-paste” of the real deal.
Scammers use these sites to trick you into a false sense of security. Because the logos, fonts, and layout look identical to the company you trust, your brain is less likely to trigger a “danger” response.
The Most Common Targets
Scammers don’t clone at random; they target industries where sensitive data or high-value transactions occur:
Banking & Finance: To capture login credentials and MFA codes.
E-commerce: To steal credit card details via fake “checkout” pages.
Government Services: To harvest Social Security numbers or charge “convenience fees” for services.
Social Media: To hijack accounts and spread further scams to friends and family.
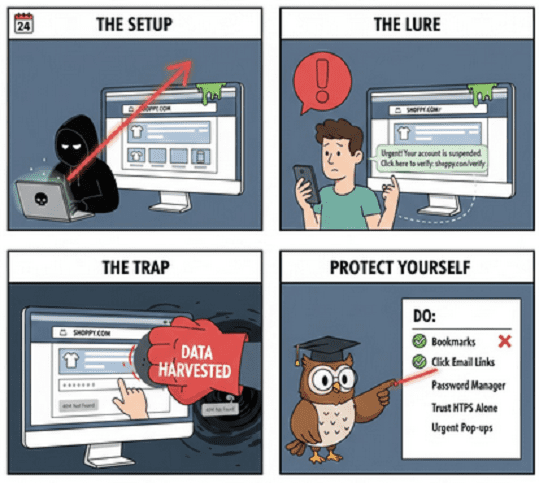
How the Scam Works: Step-by-Step
A cloning attack is rarely an isolated event; it is usually part of a coordinated “phishing” funnel.
The Replication: The scammer uses software to download the legitimate site’s code. They then host this code on a lookalike domain (for example, using a zero instead of the letter ‘o’).
The Lure: You receive an urgent email or SMS claiming there is a problem. “Your account has been suspended” or “Unusual login detected.”
The Hook: You click the link in the message, which takes you to the cloned site.
The Harvest: You enter your username and password. On the backend, the scammer’s script records your keystrokes.
The Redirect: Often, after you “log in” on the fake site, the page redirects you to the actual legitimate website. You might think it was just a glitch, but the damage is already done.
How to Spot the Imposter
While the visuals may be identical, scammers can never perfectly replicate the infrastructure of the original site. Here is what to look for:
1. Scrutinize the URL (The Address Bar)
This is the only thing a scammer cannot fully fake. Look for:
Typosquatting: Replacing letters with numbers or similar-looking characters.
Subdomain Tricks: Using the real company name as a prefix to a different domain.
Wrong TLD: Using .net or .co when the official site is .com.
2. The Padlock is Not a Guarantee
A “Lock” icon in the browser simply means the connection is encrypted; it does not mean the site is who it says it is. Scammers now use free SSL certificates to make their fake sites look “Secure.” You can click the padlock to see who the certificate was actually issued to.
3. Check for Broken Links
Scammers often only clone the login page or the homepage. If you click on the “About Us,” “Privacy Policy,” or “Terms of Service” links at the bottom and they don’t work, you are likely on a clone.
4. Grammar and “Urgency”
Legitimate companies rarely use alarmist language like “ACT NOW OR YOUR FUNDS WILL BE PERMANENTLY DELETED.” If the tone feels like it’s trying to panic you, it’s a red flag.
How to Protect Yourself
| DO | DON’T |
| Use Bookmarks: Save your bank and favorite shops to your browser and only access them through those links. | Click Email Links: Never click a link in an unsolicited “urgent” email or text. |
| Enable MFA: Use an authenticator app. Even if a scammer gets your password, they can’t get in without the code. | Trust “HTTPS”: Remember that scammers use encryption too. |
| Use a Password Manager: These tools won’t “auto-fill” credentials if the URL doesn’t match the one you saved. | Pay via Non-standard Methods: Beware of sites asking for wire transfers or gift cards. |
Remember, awareness is your strongest defense.
Contact us if you’d like more information on how cyber intelligence can help you locate scammers.
Please share this guide with friends and colleagues.
Stay up to date on the latest scam company alerts.
Advanced cyber tracking and profiling technology can identify where they are hiding.
Get in touch today and receive a free phone consultation.

Focused Stock Company (Clone of FCA authorised firm) Warning

Illuminate Trade / illuminatetrade.com Warning

Fibovest Warning | fibovest.com

Horizon Gold Warning | thehorizon-gold.com

HexaTrade | hexatrade-app.net Warning

QuickFXTrade Quick FX Trade quickfxtrade.com Warning

Standard Crypto Trading Warning | standardcryptotrading.com

Inoquant Warning | inoquant.com